Bypassing eSIM Hotspot Restrictions
This post describes a bypass of hotspot restrictions eSIM providers may impose. The technique involves tunneling traffic through a TCP relay on the phone and branching the tunnel out to a SOCKS proxy.
The Problem
Mobile devices offer the option to share their Internet connection with other devices through a feature called hotspot (tethering).
eSIM providers may argue that hotspot tethering is not possible with their cards. As I demonstrate here, this is mainly a business argument that can be bypassed.
When I recently had an eSIM card that did not provide an Internet connection to devices connected to my phone’s hotspot, I looked for a way to bypass this. I haven’t dug deep how the restriction is applied technically, but probably, it is done by discarding IP packets with a TTL value below a certain threshold.
Bypassing an LTE speed limit by overriding default TTL values has been previously discussed in this article.
This post shows a different bypass, by letting the phone act as a TCP relay. Therefore it does not require overriding the TTL.
Requirements
The bypass shown here requires a host whose SSH service is reachable from the Internet. This tutorial uses an AWS EC2 instance, but any public VPS will work. Additionally, the method requires an Android phone to install an app to act as an TCP relay. Possibly similar apps exist for Apple iOS, but I haven’t done any research on that, so I can’t comment here. It does not require a rooted phone.
The phone must enable the hotspot network and the local laptop (or any other local device) must be connected to the hotspot WiFi.
Phone Configuration
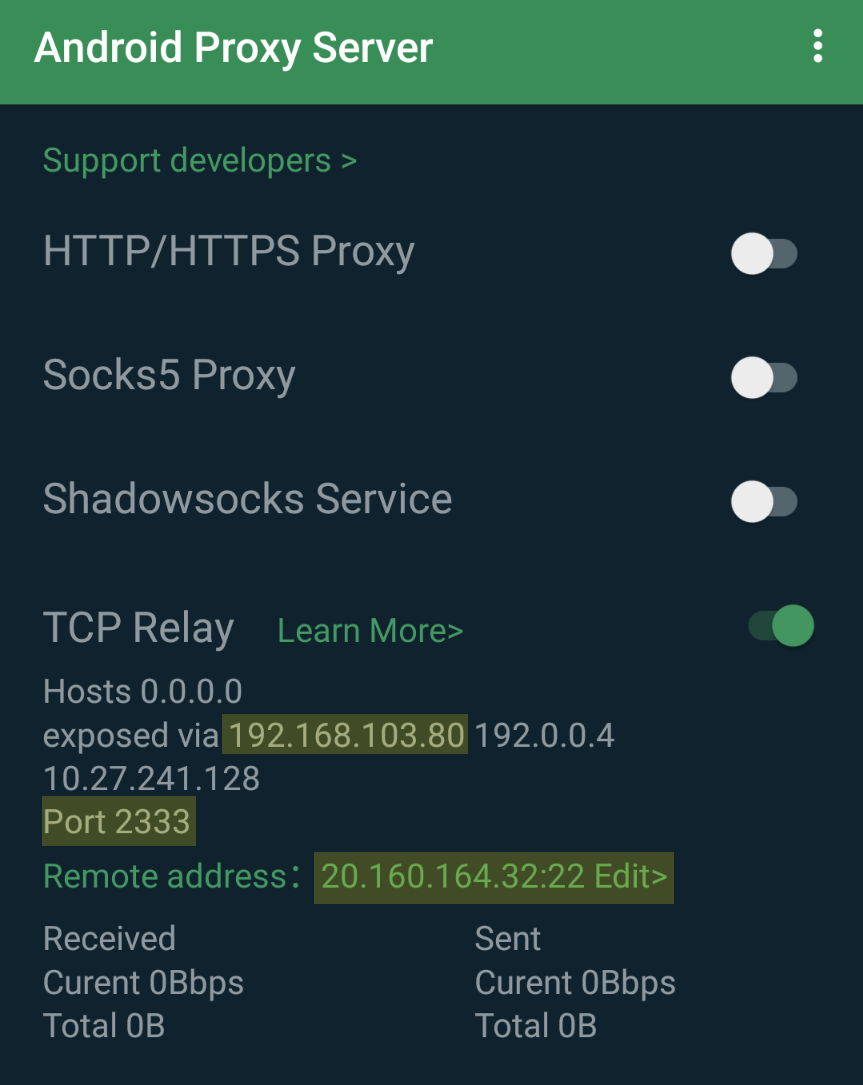
First, the phone needs to be configured to be a TCP relay. It will be configured to relay all traffic received on a TCP port to another, specifiable, address and port. I used an app called Android Proxy Server. The app is free and includes ads. The TCP relay works on a stock, non-rooted Android phone.
The following screenshot of the app shows the TCP relay option and its configuration. As the highlighted sections show, it was configured to expose 192.168.103.80:2333 (hotspot network) and relay TCP traffic to a remote IP address within an Internet address space on port 22.
Tunneling Traffic
Utilizing the tunnel, it is possible to connect via SSH to the remote host over the TCP relay:
PS C:\Users\Administrator> ssh -i key -l ubuntu -p 2333 192.168.103.80
ubuntu@ip-172-31-20-225:~$
The SSH connection is relayed by the phone to the EC2 instance:
ubuntu@ip-172-31-20-225:~$ curl -s ipinfo.io | grep org
"org": "AS16509 Amazon.com, Inc.",
Depending on the purpose, remote shell access may not be enough to perform work. In that case, it is worth to consider additional port forwarding over SSH e.g. -L 3369:localhost:3389 to tunnel RDP traffic through SSH and perform graphical tasks on the remote machine.
Branching Out The Tunnel
This method can also be used to gain Internet connectivity for browsing on the local laptop via the tunnel.
To achieve that, the tunnel can be branched out to be a SOCKS tunnel.
SSH provides this functionality by supplying the -D <port> parameter. The previous connection command becomes:
PS C:\Users\Administrator> ssh -i key -l ubuntu -p 2333 -D 10800 192.168.103.80
ubuntu@ip-172-31-20-225:~$
Port 10800 on the local laptop acts as a dynamic proxy (SOCKS). It can be used to tunnel application traffic through the remote host.
Local applications simply need to be instructed to use localhost:10800 to connect over SSH, the TCP Relay, and through the SOCKS proxy to the Internet.
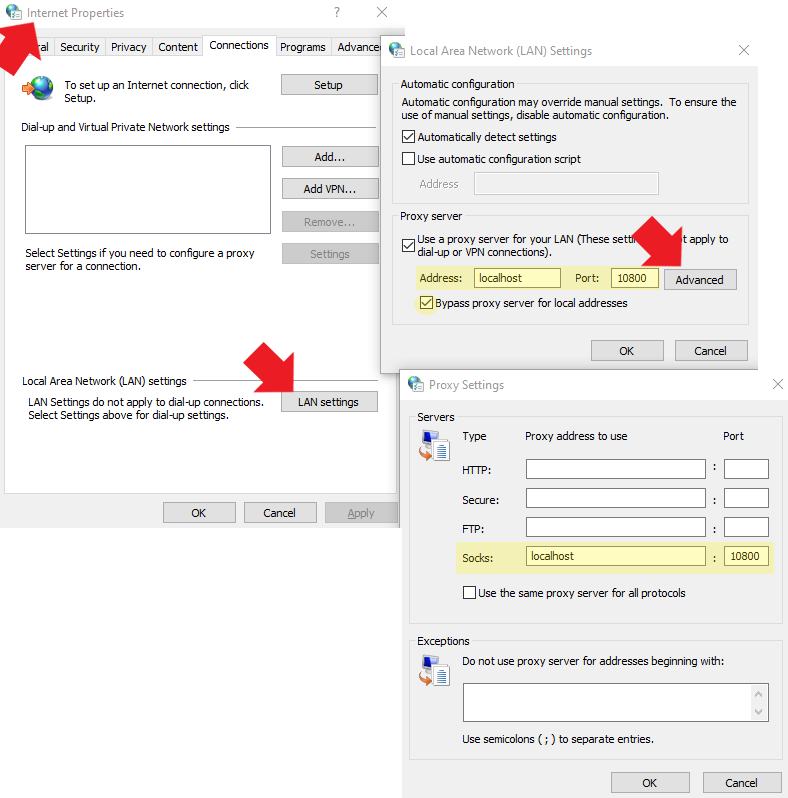
On Windows 10, the SOCKS proxy can be set system-wide in Internet Options:
On Linux, there are multiple methods available to configure the local system to tunnel traffic through the SOCKS proxy. One of the ways is to use proxychains. Simply install the program on your device, and add the SSH tunnel to the configuration file at /etc/proxychains4.conf:
# file: /etc/proxychains4.conf
<SNIP>
socks4 127.0.0.1 10800
Once configured, the traffic of selected apps can be routed through the tunnel by prefixing their launch command with proxychains:
$ proxychains firefox
Outro
Using this method of TCP relaying the SSH traffic from the phone to a cloud-based tunneling server, it is trivial to get around the hotspot restrictions. Thank you for reading.